|
|

Why would you want to setup a Local Area Network (LAN)?
The main reason for doing that is the capability of simultaneously connect a number of devices to the same Internet access.
In a household, different members of the family can have simultaneous access to the Internet with their own devices: computers, smart phones, tablets and other smart devices that can be found today in any household.
In a small office, all the employees can connect simultaneously to the Internet with their computers.
Also, some devices can be shared across the LAN. For example printers and Network Attached Storage (NAS) devices.
The local network could also host some specialized server, like a database in an office environment, a media server in a household, a security system, a VoIP telephone (Internet phone), or a video game system.
Main component of a network is the router. That can be just wired, or wireless, or both. Usually the latter is the most used kind. The router is the device that regulates the traffic of data across the various elements of the network, and also acts as a gateway to the external world, the Internet. Usually, a router for a home network or a small office puts together one or more additional capabilities like the ones in the following list:
- A non-authoritative DNS server. This is the network element that is capable of translating a URL into an IP address. The DNS inside a router operates usually as a cache-only device. In other words, whenever a device in the network requests a translation, it proxies the requests to a DNS server in the Internet that knows how to do the translation. Then, when it receives the response, it gives it back to the device that requested it, and it also saves it for a certain amount of time in its cache memory. That way, if another request is done for the same URL, it won’t need to go again to the higher level DNS to get the response. Instead, it will be able to get it from its own cache.
- A DHCP server. This is the network device that assigns the IP addresses to all other devices in the same local network or the same subnet. These IP addresses can be automatically generated, within the range of the assigned subnet, or can be fixed IP addresses, or IP addresses that are always assigned to the same network device. These are sometimes called reserved IP addresses.
- A NAT server, or Network Address Translation server. This server translates the IP addresses of each local devices to the single address assigned by the service provider to your modem. Vice versa, when a packet comes in from the outside, it converts the single address back into the address of the device that is really supposed to receive the packet. This device is also useful from the perspective of security, because it shields the whole local network from the outside world, so from the outside world it is not possible to know how many devices are available in the local network and it is more difficult to reach them.
- A VPN server, or Virtual Private Network server. This can be used to securely reach the local network from the Internet, emulating a dedicated channel where all the packets going back and forth are encrypted.
- A Media Server, usually supporting the DLNA standard (Digital Living Networking Alliance). Such service is able to easily distribute your media contents across all the devices in your network.
An finally, these are the steps that are needed to setup a LAN. These step are basically the same for both a household or a small office:
- Connect the router to the Cable Modem or the DSL Modem. This is usually rented from the Service Provider, but it is usually possible to buy one and configure it according to the Service Provider instructions. Other times, the router and the modem are bundled together in a single device, and therefore this step would not be required for those cases.
- Configure the router. This is the step where the Local Area Network is defined. It is also recommended to lock down the router, i.e. change its password and enable its internal firewall, to secure the devices within the LAN.
- Configure the WiFi security.
- Configure the IP addresses. For very simple home networks, this step might be to just set the range of IP addresses used by the DHCP server inside the router. In more complex networks, it is possible to configure static IP addresses for certain elements of the network. The latter is also sometimes called DHCP reservation.
- Setup user accounts. This is a step mostly dedicated to small businesses.
- Configure and connect devices to the network. This step considers both wired and wireless devices. In case of many wired devices, rather than connecting all of them directly to the router, another option is to connect them to one or more HUBs or Ethernet switches and then connect the HUBs or switches to the router.
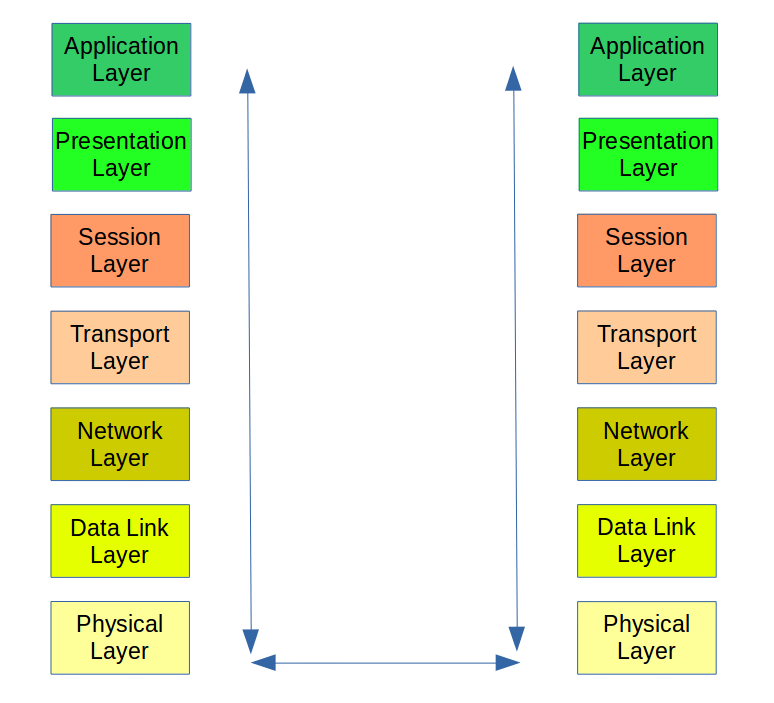 Transmission protocols are designed to work in collaboration at various levels. Transmission protocols are designed to work in collaboration at various levels.
For example, there are those protocols that provide transportation capability, thus identifying where the destination of a piece of data is located and routing it appropriately to it. Then there are other protocols that oversee the information sent across the Internet and make sure that different pieces of information are received in the correct order by the applications requesting it.
An established Reference model called OSI, or Open System Interconnection, establishes the criteria used to identify each specific protocol and its functionality. Any communication protocol in existence today, can be identified under one of the seven layers defined by OSI.
Here is the list of the OSI layers:
- Physical Layer. It is the communication protocol at its most elementary level. It provides the hardware necessary to transmit and receive data. This hardware takes care of establishing the lower level format of the communication, a bit stream across a medium that can be a cable, or a radio signal, or even the light itself (in the fiber optics, for example).
- Data-Link Layer. This is a communication protocol that organizes the raw data transmitted by the layer 1 into frames, which are blocks of subsequent bits.
- Network Layer. This layer handles the addressing of the information, allowing the data to be sent from a specific end point and received by another specific end point. For example, the IP protocol is the level 3 protocol used in the Internet.
- Transport Layer. This layer is the one that organizes the data in packets, including possible extra data to make sure packets are sent and received in the correct order and without errors. TCP and UDP are examples of layer 4 protocols used in the Internet.
- Session Layer. This is the protocol layer used to initiate and terminate conversations. They also take care of authentication, to make sure data is received by the entity that was designated by the sender. In the Internet, this is a function that is usually made available by the same TCP and UDP protocols that provide the layer 4. TCP and UDP, therefore, are usually indicated as layer 3/4 protocols. Note that while OSI provides a precise reference of how data transmission should be organized in the networks, protocols don’t necessarily provide such a specialized form. Sometimes, protocols lay in between or encompass more than one OSI layer.
- Presentation layer. This is the layer that provides a translation of the data from one form to another. For example, a translation between a format that is better suited to the transmission of the information through the Internet, and a format that is better suited for consumption of the data by a human being. HTML is one of such protocols, widely used to serve web pages to people.
- Application Layer. Applications are the topmost consumers of data. Two applications running on separated computers in different locations talk to each other through layer 7, using the services of all the underneath layers.
The implementation of a set of protocols that work in concert to transfer data from one location to another, and from one user to another, is called Protocol Stack. A pictorial representation of a stack is a series of layers, each one identifying an OSI layer. In the stack, each layer represents a specific protocol, in the OSI reference model. Protocols of the same layer talk to each other by the means of their underneath layers.
The top layer is the creator or the consumer of data. Once the data is created is passed to the immediately lower layer, which adds some extra information to handle the data according to its functionality. While going down through the stack, each layer keeps adding its own information, in a sort of envelops that enclose the data coming from the above levels. On the consumer side the opposite happens, each layer passes the data to its immediately upper layer after removing its envelop of data, up up until the topmost layer receives the data in the format that it can understand.
 Since in my previous post I have talked about issues related to the deployment of WiFi networks, it is only fair if I step back a bit and provide some explanations about WiFi standards and how and why they are regulated. Since in my previous post I have talked about issues related to the deployment of WiFi networks, it is only fair if I step back a bit and provide some explanations about WiFi standards and how and why they are regulated.
Wireless standards are those related to the wireless communications in general, and in particular:
There are two main bodies in the world that promote wireless standards. They are the FCC in the United States and the ETSI in Europe. Most of the other countries abide to the regulations of these two main bodies, but also participate in the definition of the standards themselves.
This is all done to guarantee that wireless devices, when moving from one location to another, always respect the local rules (frequencies, channels bandwidth, type of encoding, and so forth) so that they can connect to the wireless networks almost seamlessly.
Companies that build the wireless devices must abide to the same rules to guarantee their own customers that they can connect to the networks wherever they are and whatever is the brand of the network devices through which they access the wireless networks. Think, for example, if a WiFi router was built using a protocol that only other devices of the same brand could understand. It would be totally useless and nobody would buy it. Who would want a router that does not allow you to connect your smart-phone, or your laptop, or your tablet?
Specifically for WiFi communications, and in addition to the governing bodies FCC and ETSI, the WiFi Alliance, which is a non-profit consortium of several constructors, oversees the correct application of the IEEE 802.11 standards for WiFi communications. They do so by promoting the adoption of these standards by all the industries, and also by providing a certification program for the WiFi devices.
The currently most used standards of the IEEE 802.11 are:
- 802.11a, with rated bandwidth of 11 Mbps, or about 1.4 MBps
- 802.11b, with rated bandwidth of 11 Mbps, or about 1.4 MBps
- 802.11g, with rated bandwidth of 54 Mbps, or about 6.75 MBps
- 802.11n, with rated bandwidth of 300 Mbps, or about 37MBps
- 802.11ac, with rated bandwidth of 1.331 Gbps, or about 166MBps
Most people is familiar with these names nowadays, because they find them used in their home routers, or computers, or even the smart-phones. On the other end, 802.11 standards are continuously updated and a new standard comes out so often, allowing for continuously incrementing the bandwidth they can provide, and increasing their level of security.
People that works in the networking field needs to keep themselves continuously updated on the latest evolution of the standards, if they want to be able to satisfy their customers and stay ahead of the competition.It is really easy to find costly installations that do not work properly because some detail was not given the proper consideration when designing the network, like throughput vs. bandwidth, or cross-interference from adjacent channels, or race conditions caused by access points that compete with each other in providing access to portable devices.
Dazzling Solutions is always available to provide consultation on the subject, as well as providing support for designing new WiFi networks or upgrade them to bring them to the state of the art and maximize their performance. Please contact us for a free estimate.
|
DZgameEngine Repository
on GitHub
|
|


 Transmission protocols are designed to work in collaboration at various levels.
Transmission protocols are designed to work in collaboration at various levels. Since in my previous post I have talked about issues related to the deployment of WiFi networks, it is only fair if I step back a bit and provide some explanations about WiFi standards and how and why they are regulated.
Since in my previous post I have talked about issues related to the deployment of WiFi networks, it is only fair if I step back a bit and provide some explanations about WiFi standards and how and why they are regulated.

